Megalines Insurance And Risk Advisers
For over 12 years, we have been relentless in building quality and effective Insurance programs for our teeming Clients in various Industries and of every size.
Cyber Insurance for Families
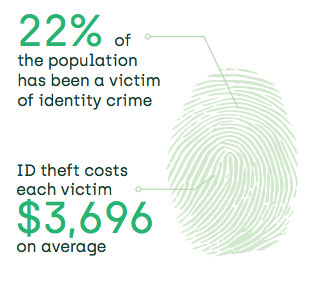
Technology is now part of our everyday lives and as 2020 has shown essential for communication, shopping and managing a family's busy schedule. We are heavily reliant on technology.
Dependence on the Internet, the growth of web-enabled devices and the use of social media means that people are much more interconnected. This introduces new risks into our homes and lives that must be managed.
Personal Cyber Insurance goes beyond computers, laptops and mobile devices. It covers you, your family, your identity, your reputation , your money and your time (wage replacement) when a cyber event occurs.
As technology use grows in our lives, protecting yourself and your family against cyber risk and attack has become more important. Make the effort and take the time to secure against risks such as malware, viruses, cyber espionage, denial of service attacks, cyber theft, identity theft and more. For extra peace of mind consider Personal Cyber Protection Insurance as part of your household's cyber risk mitigation and recovery strategy.
Cyber crime is highly specialised and ever evolving - cyber insurance can cover you for many aspects of cyber crime such as:
A cyber event includes:
Further to technical cyber threats , social media can also become an area for anti-social behaviour
The product also responds to:
Questions and case studies
Sarah was working on her computer when she clicked on a plausible email attachment which unleashed a malware virus. As a result, this locked all of her important files. As a result, Sarah was unable to access the files on her computer unless she paid a Ransom of $10,000.
Cyber Insurance provides cover for cyber event response costs to remove the virus, restore data, and secure the home IT. An IT expert who specialises in ransomware attacks would be appointed to remove the malware and get Sarah\'s computer operational again.
Daniel received an email on his computer allegedly from a popular social media platform stating he needed to verify his account by clicking on the provided link. Daniel clicked on the link, and a couple of days later he was unable to log in to his social media accounts. As it turns out, Daniel had downloaded malware onto his computer that allowed a cybercriminal to steal Daniels\' personal information and identity
Cyber Insurance provides cover for cyber event response costs to remove the virus, restore data, and secure the home IT. The policy would also provide identity theft response costs to help the policyholder re-establish their identity and essential records. If Daniel had to take time off work to rectify his personal records and lost wages as a result, he could be entitled to wage replacement benefits as part of his claim.
Robin received an email on her computer that looked like it was from her bank. The email required Robin to download an attachment to \'verify\' her account details. It turns out, the email was not from Robin\'s bank, it was a fake email from a hacker. The attachment Robin downloaded was a keylogger virus that recorded Robin\'s login details for various accounts including the login to her bank account. The hacker then gained access to Robin\'s bank account and transferred $5,000 from Robin\'s account to their own.
Cyber Insurance provides cover for policyholders\' funds that are transferred as a result of cyber theft. Personal Cyber Protection Insurance also provides cover for cyber event response costs to remove the virus, restore data, and secure the policyholder\'s home IT.
Jess just started high school. Within the first few weeks, she became a victim of bullying. It started out as a few comments, however quickly escalated to repeated harsh and vile comments on all of her social media profiles. The online bullying had a significant impact on Jess and led to her not wanting to go to school and a deterioration in her grades.
Personal Cyber Insurance provides cover for a policyholder and their spouse to attend critical guidance sessions if their child is subjected to cyber bullying. In this case, these sessions would help Jess\'s family work through this ordeal and better deal with any future instances of cyberbullying. The policy would also cover the costs to try to remove the hurtful comments. The policy would also provide a wage replacement benefit if the parents have to take unpaid time off work to attend guidance sessions or to meet with the school or other authorities to deal with the incident.